In this blog we will setup a new VPC. In this VPC, we will create a Public and a Private Subnet. The way we will configure them is that any EC2 in the Public Subnet will have a Public and Private IP address, while any EC2 in the Private Subnet will have only a Private IP address associated with it. We can connect to the EC2 in the Public Subnet as it has a Public IP, but how do we connect to the EC2 in the Private Subnet as it doesn't have a Public IP? This might be required for making any changes to that particular EC2 instances to perform tasks like installing/upgrading databases etc.
One way to it to setup a VPN connection between the Laptop and the VPC as mentioned in the previous blog. This way the Laptop and the EC2 in the Private Subnet will appear as though they are in the same network and so we would be able connect from the Laptop to the EC2 in the Private Subnet. Another way is to connect to the EC2 in the Public Subnet using the Public IP and from there connect to the EC2 in the Private Subnet using the Private IP. This is what we would be exploring in this blog.
Step 1: Go to the EC2 Management Console and make sure the "New EC2" experience is selected.
Step 2: Click on the "Key Pairs" and click on "Create key pair". Enter the Key pair name and make sure the ppk format is selected and click on "Create key pair".
The Key pair would be created as shown below.
Step 3: Click on "Elastic IPs", click on "Allocate Elastic IP address" and finally click on Allocate. The Elastic IP address is required for NAT instance which will be automatically created while creating the VPC later.
An Elastic IP address will be created as shown below.
Step 4: Go to the VPC Management Console and click on "Launch VPC Wizard".
Step 5: Select "VPC with Public and Private Subnets" Option and click on Select.
Step 6: Enter the name of the VPC as MyVPC and select the Elastic IP created in the previous steps. Finally, click on "Create VPC". Rest of the default options are good enough.
The VPC creation process process takes a few minutes and the VPC screen will be updated as shown below.
Step 7: Any EC2 created in the Public Subnet, will only have the Private IP, we need to make sure it also has a Public IP address. For this to happen, from the list of Subnets select the Public Subnet, Actions -> "Modify auto-assign IP settings".
Make sure to check "Auto-assign IPv4" and click on Save.
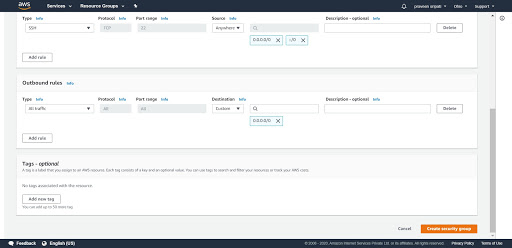
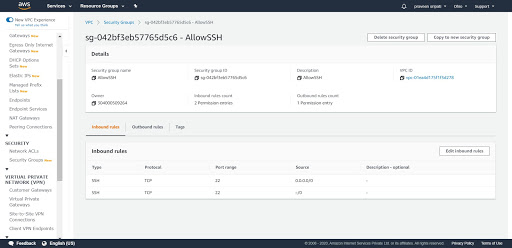
Step 8: Click on the Security Groups and click on "Create security group". Enter the name as AllowSSH, give some description and add an inbound rule as displayed below to allow Port 22/ssh inbound. Make sure to select the VPC which has been created in the previous steps. Click on "Create security group". This one will be associated with the EC2 instances later.
Step 9: Create Ubuntu EC2 instances with t2.micro as the instance type in the MyVPC, one each in Private and Public Subnets. Make sure to select MyVPC and the appropriate Subnet in 'Configure instance' options while creating the EC2 instance. Also, select the AllowSSH Security Group and the KeyPair which has been created in the previous steps, this allows us to connect to the EC2 via SSH using the Key pair.
Step 10: Name the EC2 instances as MyVPC-PublicSubnet and MyVPC-PrivateSubnet appropriately. Also notice that the EC2 in the Public Subnet has both Private and Public IP address, while the EC2 in the Private Subnet has only Private IP address as shown below.
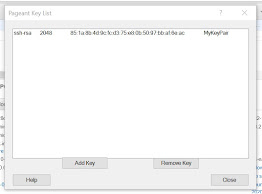
Step 11: Download putty.exe and pagent.exe from here. There is no need to install any of these softwares, simply download them. Start the pagent.exe and add the ppk file which has been downloaded in one of the previous steps.
Step 12: Open putty.exe and in the Host Name field enter the username ubuntu and the Public IP address of the EC2 in the Public Subnet separated by the symbol @ as shown below.
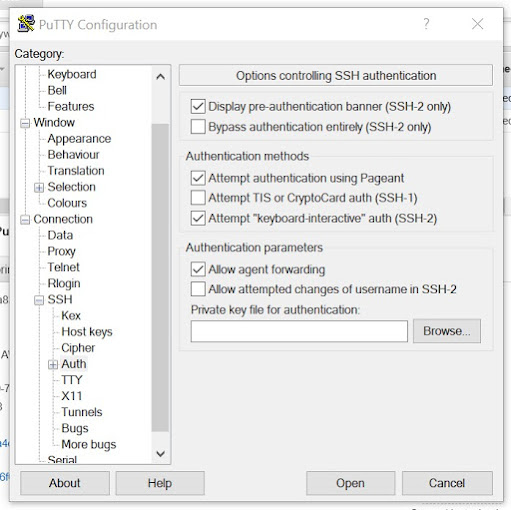
Step 13: Go to Connection --> SSH --> Auth and make sure to select "Allow agent forwarding" and click on Open to connect to the EC2 instance in the Public Subnet. There is no need to specify the Private key as it has been specified in the pagent.exe.
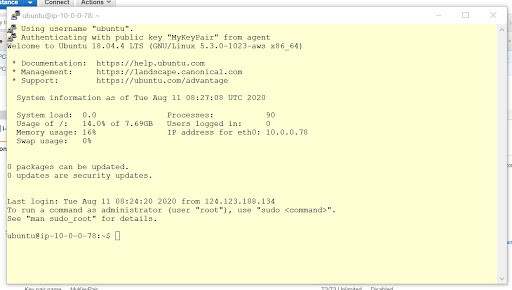
Step 14: From the Putty session execute the below command to connect to the EC2 in the Private Subnet. Make sure to replace 1.2.3.4 with the Private IP address of the EC2 in the Private Subnet. Note that there is no need to specify the Private key this time also as it is from the pagent.exe. Now on this EC2 instance we should be able to install any back-end applications like database, business logic and so on.
ssh ubuntu@1.2.3.4
- Terminate the EC2 instances
- Delete the NAT Gateway
- Wait for a few Minutes
- Delete ElasticIP
- Finally delete the VPC



















No comments:
Post a Comment